DSN: Ransomware News - Even more dangerous: NotPetya
As you may have heard, a new, more complex, and more dangerous variant of the WannaCry Virus was released. This new attack called "NotPetya" or "Goldeneye" exploits the same vulnerability that WannaCry used to spread itself and relies primarily on email phishing (e.g. "check out this great attachment") to infect a network. Unfortunately, while WannaCry's many design flaws caused it to flame out after a few days, this latest ransomware threat doesn't make the same mistakes. The reason that this is more dangerous is that once inside the network, the ransomware steals administrative credentials, giving it control over powerful system management tools like Windows PsExec and Windows Management Instrumentation. Researchers are still trying to figure out the details but they agree that NotPetya is much more dangerous and harder to protect against.
Sophos and Symantec both have "rapidly released" signatures and will detect NotPetya. Clients using Sophos' intercept X should be protected from the encryption process. But this doesn't mean that the infection still can't enter and spread within your network. More details on what users may see are below.
Langtech urges you to remind your users of best practices when it comes to cybersecurity, which include, but are not limited to:
- Never click on a link or email attachment if you were not expecting it or until you verify through other means that it's legitimate.
- Don't download or store sensitive information on personally owned equipment.
- Establish a verification system that requires multiple authentication to confirm money transfer requests
- Make sure your Microsoft systems are patched to the latest versions
Educating your employees on cybersecurity continues to be the best defense, however, we recommend a combination of next generation endpoint security (anti-virus, spam filtering, behavioral analytics, etc), mobile device management, network security policies, backups, and encryption detection software to combat the problem. Please contact us if you have any questions/concerns or would like a consultation to ensure you have the best defenses in place.
More Details:
There will be some warning of the disk being encrypted in the event of infection. Users see the following screen on their workstation:
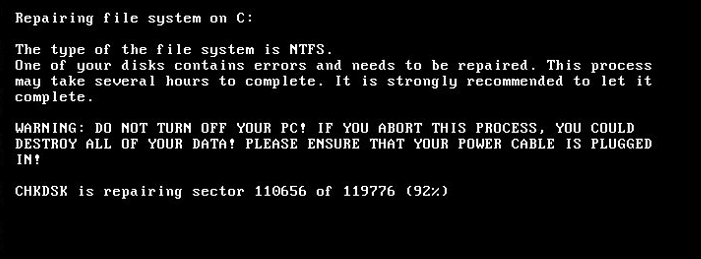
If this is seen, you need to turn off the workstation immediately (aka unplug the power) and call Langtech.
Once you see the screen below, it's too late. At that point, all we can do is re-image the workstation and restore from backup: